***The Iowa Standard is an independent media voice. We rely on the financial support of our readers to exist. Please consider a one-time sign of support or becoming a monthly supporter at $5, $10/month - whatever you think we're worth! If you’ve ever used the phrase “Fake News” — now YOU can actually DO something about it! You can also support us on PayPal at [email protected] or Venmo at Iowa-Standard-2018 or through the mail at:
PO Box 112
Sioux Center, IA 51250
On the second day of the event, we finally got down to business of looking at data. But what are we looking at?
I’ve explained at length below. Feel free to reply if you have any questions!—Rep. Jonathon Hill.
Packet captures
A packet capture is simply a digital record of a packet of data that is transmitted on a computer network.
These packets contain:
- The data being transmitted itself, which may or may not be encrypted
- The addresses of the sender and recipient computers
- The timestamp the packet was sent
- Other information about the data, such as format of the request, and the requested format of the response
When Mike Lindell claims to have multiple terabytes worth of PCAPs, that is potentially significant for the following reasons:
- It could show intrusions into election systems.
- It could show that the election systems themselves were illegally connected to or accessed from the internet.
- It could provide proof that votes or vote counts were altered.
So far, I still have not seen the first byte of packet capture data, but I’m told that there are still people in the back trawling through it.
Hopefully they will let me back there to watch them work.
Forensic images
A new type of data, hitherto unmentioned, was unveiled today: forensic images of a hard drive from a Mesa, CO Dominion voting machine from before, during, and after the election.
A whistleblowing Mesa County clerk’s office was raided yesterday while she was en route to speak at the Symposium.
A forensic image is an exact digital copy (a snapshot, essentially) of a hard drive. This copy can be accessed just like a hard drive itself, but the contents cannot be altered.
Hacker/whistleblower Ron Watkins (CodeMonkeyZ) and other tech experts opened two of these forensic images and explored them on screen.
The audience participated by watching and asking questions.
What kinds of data are of interest?
Log files
- Three years worth of Microsoft Internet Information Server 10.0 access logs spanning 2019-2021 were discovered, demonstrating that web server software ran on the machine during that period of time.
- These logs demonstrate that a SOAP-based web service ran and was accessed multiple times on the machine. These requests come from IPv6 IP addresses, which suggests (but does not prove) that the origin of the traffic was another machine on a private network rather than the internet.
- Windows and Dominion software update logs should provide clues to the versions of the Windows operating system and software running, which can then be analyzed for known security vulnerabilities. These vulnerabilities could suggest the means of entry whereby a hacker could have gained access.
Configuration files
- These files control how the software operates and can turn certain features on or off.
- All configuration files need to be audited for any options that might enable or allow internet connectivity or remote access to the web services that were running on the machine.
Batch scripts
- These are plain text files that contain a series of commands to alter configuration in an automated way.
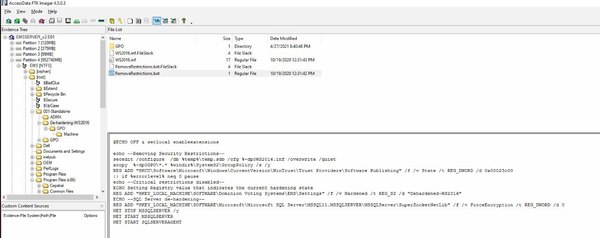
- A VERY interesting file was found called RemoveRestrictions.bat was filed, which appears to disable encryption of the voter database on the machine. When run, the script outputs a message that says “Critical restrictions disabled.” Why would a file like this be present on the machine pre-update, and how did it get there?
Databases
- These files would likely contain all the voter data, votes and ballot data, staff logins, permissions, audit logs, and more.
- Database transaction logs, if present, would show each and every change to the database—how, when, and by whom. This data could be replayed to discover the sequence of events before, during, and after election day. Such data could be highly significant.
Source code
- With hints from the logs files and configuration files, it should be possible to find the files that make up the software of the Dominion system itself—especially the web services that were accessed.
- These files should provide clues as to the technologies and languages used to develop the software. Raw source code could be analyzed, and compiled software could be decompiled. With source code in hand, a software developer could analyze these files and correlate them against the access logs to see what actions were performed remotely, and when.
Don’t make me leave empty-handed
Thanks to certain contacts, I was able to chat with Professor David Clements during this examination of files.
I asked if Lindell’s team would be publishing copies of the data online for anyone to examine first hand, he waved at the screen and asked “what do you call this?”
In reply, I said, “it’s interesting, but not yet conclusive.”
This seemed to offend him, as if I’d insulted their work, but I hastened to explain:
“Before I can stake my reputation on something I need the opportunity to download and examine a copy of the data myself. If I can do this, you’ll have the biggest advocate you could possibly want in South Carolina.”
Hopefully I will be able to connect with one or more of the white-hat hackers on the team today and download a copy of either the PCAP data or the forensic images, or both.
If these data are real, they should have no problem sharing it, right?
What we do NOT need to prove
Remember, I came here to try to personally answer this question:
Was the 2020 election hacked?
To put this question to rest, I need first-hand evidence. Evidence that I can see, touch, and interact with.
Here’s what doesn’t need to be proven to me, however:
We must do much more to protect the integrity of future elections.
You can count on me to be an advocate for the strongest possible election laws and systems.
I was an advocate for paper hand-countable ballots long before November 2020, and will continue to advocate for secure elections regardless of what transpires this week.
Sincerely,
Rep. Jonathon Hill